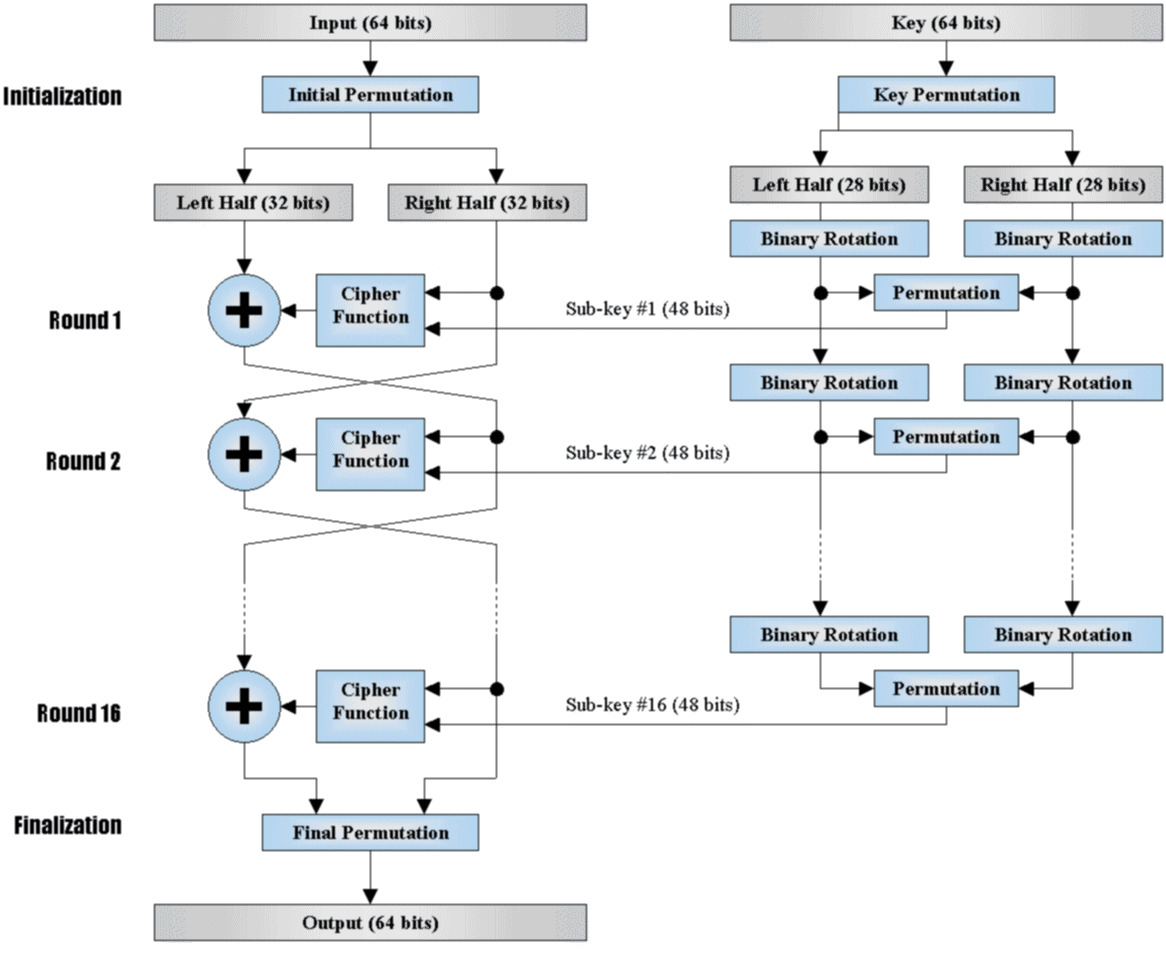
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
141
142
143
144
145
146
147
148
149
150
151
152
153
154
155
156
157
158
159
160
161
162
163
164
165
166
167
168
169
170
171
172
173
174
175
176
177
178
179
180
181
182
183
184
185
186
187
188
189
190
191
192
193
194
195
196
197
198
199
200
201
202
203
204
205
206
207
208
209
210
211
212
213
214
215
216
217
218
219
220
221
222
223
224
225
226
227
228
229
230
231
232
233
234
235
| from typing import List
# IP置换表
IP = [58, 50, 42, 34, 26, 18, 10, 2,
60, 52, 44, 36, 28, 20, 12, 4,
62, 54, 46, 38, 30, 22, 14, 6,
64, 56, 48, 40, 32, 24, 16, 8,
57, 49, 41, 33, 25, 17, 9, 1,
59, 51, 43, 35, 27, 19, 11, 3,
61, 53, 45, 37, 29, 21, 13, 5,
63, 55, 47, 39, 31, 23, 15, 7]
# 逆IP置换表
IP_INV = [40, 8, 48, 16, 56, 24, 64, 32,
39, 7, 47, 15, 55, 23, 63, 31,
38, 6, 46, 14, 54, 22, 62, 30,
37, 5, 45, 13, 53, 21, 61, 29,
36, 4, 44, 12, 52, 20, 60, 28,
35, 3, 43, 11, 51, 19, 59, 27,
34, 2, 42, 10, 50, 18, 58, 26,
33, 1, 41, 9, 49, 17, 57, 25]
# 扩展置换E表
E = [32, 1, 2, 3, 4, 5,
4, 5, 6, 7, 8, 9,
8, 9, 10, 11, 12, 13,
12, 13, 14, 15, 16, 17,
16, 17, 18, 19, 20, 21,
20, 21, 22, 23, 24, 25,
24, 25, 26, 27, 28, 29,
28, 29, 30, 31, 32, 1]
# P盒置换表
P = [16, 7, 20, 21, 29, 12, 28, 17,
1, 15, 23, 26, 5, 18, 31, 10,
2, 8, 24, 14, 32, 27, 3, 9,
19, 13, 30, 6, 22, 11, 4, 25]
# PC-1置换表(密钥初始置换)
PC1 = [57, 49, 41, 33, 25, 17, 9,
1, 58, 50, 42, 34, 26, 18,
10, 2, 59, 51, 43, 35, 27,
19, 11, 3, 60, 52, 44, 36,
63, 55, 47, 39, 31, 23, 15,
7, 62, 54, 46, 38, 30, 22,
14, 6, 61, 53, 45, 37, 29,
21, 13, 5, 28, 20, 12, 4]
# PC-2置换表(子密钥生成)
PC2 = [14, 17, 11, 24, 1, 5,
3, 28, 15, 6, 21, 10,
23, 19, 12, 4, 26, 8,
16, 7, 27, 20, 13, 2,
41, 52, 31, 37, 47, 55,
30, 40, 51, 45, 33, 48,
44, 49, 39, 56, 34, 53,
46, 42, 50, 36, 29, 32]
# 左移位数表
SHIFT_SCHEDULE = [1, 1, 2, 2, 2, 2, 2, 2, 1, 2, 2, 2, 2, 2, 2, 1]
# S盒定义(8个)
S_BOX = [
# S1
[[14, 4, 13, 1, 2, 15, 11, 8, 3, 10, 6, 12, 5, 9, 0, 7],
[0, 15, 7, 4, 14, 2, 13, 1, 10, 6, 12, 11, 9, 5, 3, 8],
[4, 1, 14, 8, 13, 6, 2, 11, 15, 12, 9, 7, 3, 10, 5, 0],
[15, 12, 8, 2, 4, 9, 1, 7, 5, 11, 3, 14, 10, 0, 6, 13]],
# S2
[[15, 1, 8, 14, 6, 11, 3, 4, 9, 7, 2, 13, 12, 0, 5, 10],
[3, 13, 4, 7, 15, 2, 8, 14, 12, 0, 1, 10, 6, 9, 11, 5],
[0, 14, 7, 11, 10, 4, 13, 1, 5, 8, 12, 6, 9, 3, 2, 15],
[13, 8, 10, 1, 3, 15, 4, 2, 11, 6, 7, 12, 0, 5, 14, 9]],
# S3
[[10, 0, 9, 14, 6, 3, 15, 5, 1, 13, 12, 7, 11, 4, 2, 8],
[13, 7, 0, 9, 3, 4, 6, 10, 2, 8, 5, 14, 12, 11, 15, 1],
[13, 6, 4, 9, 8, 15, 3, 0, 11, 1, 2, 12, 5, 10, 14, 7],
[1, 10, 13, 0, 6, 9, 8, 7, 4, 15, 14, 3, 11, 5, 2, 12]],
# S4
[[7, 13, 14, 3, 0, 6, 9, 10, 1, 2, 8, 5, 11, 12, 4, 15],
[13, 8, 11, 5, 6, 15, 0, 3, 4, 7, 2, 12, 1, 10, 14, 9],
[10, 6, 9, 0, 12, 11, 7, 13, 15, 1, 3, 14, 5, 2, 8, 4],
[3, 15, 0, 6, 10, 1, 13, 8, 9, 4, 5, 11, 12, 7, 2, 14]],
# S5
[[2, 12, 4, 1, 7, 10, 11, 6, 8, 5, 3, 15, 13, 0, 14, 9],
[14, 11, 2, 12, 4, 7, 13, 1, 5, 0, 15, 10, 3, 9, 8, 6],
[4, 2, 1, 11, 10, 13, 7, 8, 15, 9, 12, 5, 6, 3, 0, 14],
[11, 8, 12, 7, 1, 14, 2, 13, 6, 15, 0, 9, 10, 4, 5, 3]],
# S6
[[12, 1, 10, 15, 9, 2, 6, 8, 0, 13, 3, 4, 14, 7, 5, 11],
[10, 15, 4, 2, 7, 12, 9, 5, 6, 1, 13, 14, 0, 11, 3, 8],
[9, 14, 15, 5, 2, 8, 12, 3, 7, 0, 4, 10, 1, 13, 11, 6],
[4, 3, 2, 12, 9, 5, 15, 10, 11, 14, 1, 7, 6, 0, 8, 13]],
# S7
[[4, 11, 2, 14, 15, 0, 8, 13, 3, 12, 9, 7, 5, 10, 6, 1],
[13, 0, 11, 7, 4, 9, 1, 10, 14, 3, 5, 12, 2, 15, 8, 6],
[1, 4, 11, 13, 12, 3, 7, 14, 10, 15, 6, 8, 0, 5, 9, 2],
[6, 11, 13, 8, 1, 4, 10, 7, 9, 5, 0, 15, 14, 2, 3, 12]],
# S8
[[13, 2, 8, 4, 6, 15, 11, 1, 10, 9, 3, 14, 5, 0, 12, 7],
[1, 15, 13, 8, 10, 3, 7, 4, 12, 5, 6, 11, 0, 14, 9, 2],
[7, 11, 4, 1, 9, 12, 14, 2, 0, 6, 10, 13, 15, 3, 5, 8],
[2, 1, 14, 7, 4, 10, 8, 13, 15, 12, 9, 0, 3, 5, 6, 11]]
]
def str_to_bits(text: str, size: int) -> List[int]:
"""将字符串转换为位列表"""
bits = []
for i in range(size):
byte = i // 8
bit = 7 - (i % 8)
if byte < len(text):
bits.append((ord(text[byte]) >> bit) & 1)
else:
bits.append(0)
return bits
def hex_to_bits(hex_str: str, size: int) -> List[int]:
"""将十六进制字符串转换为位列表"""
bits = []
hex_str = hex_str.replace(" ", "").replace("0x", "").zfill(size//4)
for char in hex_str:
val = int(char, 16)
for i in range(3, -1, -1):
bits.append((val >> i) & 1)
return bits[:size]
def bits_to_hex(bits: List[int]) -> str:
"""将位列表转换为十六进制字符串"""
hex_str = ""
for i in range(0, len(bits), 8):
byte = 0
for j in range(8):
if i+j < len(bits):
byte = (byte << 1) | bits[i+j]
hex_str += f"{byte:02X}"
return hex_str.lower()
def permute(bits: List[int], table: List[int]) -> List[int]:
"""按置换表进行置换"""
return [bits[table[i]-1] for i in range(len(table))]
def left_shift(bits: List[int], n: int) -> List[int]:
"""循环左移"""
return bits[n:] + bits[:n]
def generate_subkeys(key_bits: List[int]) -> List[List[int]]:
"""生成16个子密钥"""
# PC-1置换
key_pc1 = permute(key_bits, PC1)
# 分成左右两部分
C = key_pc1[:28]
D = key_pc1[28:]
subkeys = []
for round_num in range(16):
# 循环左移
shift = SHIFT_SCHEDULE[round_num]
C = left_shift(C, shift)
D = left_shift(D, shift)
# PC-2置换生成子密钥
combined = C + D
subkey = permute(combined, PC2)
subkeys.append(subkey)
return subkeys
def f_function(R: List[int], K: List[int]) -> List[int]:
"""f函数"""
# 扩展置换E
R_expanded = permute(R, E)
# 与子密钥异或
xor_result = [R_expanded[i] ^ K[i] for i in range(48)]
# S盒替换
sbox_output = []
for i in range(8):
# 取6位
block = xor_result[i*6:(i+1)*6]
row = (block[0] << 1) | block[5]
col = (block[1] << 3) | (block[2] << 2) | (block[3] << 1) | block[4]
val = S_BOX[i][row][col]
# 转换为4位
sbox_output.extend([(val >> 3) & 1, (val >> 2) & 1, (val >> 1) & 1, val & 1])
# P盒置换
return permute(sbox_output, P)
def des_encrypt(plaintext_bits: List[int], key_bits: List[int]) -> List[int]:
"""DES加密"""
# 初始置换IP
bits = permute(plaintext_bits, IP)
# 生成子密钥
subkeys = generate_subkeys(key_bits)
# 分成左右两部分
L = bits[:32]
R = bits[32:]
# 16轮迭代
for i in range(16):
L_next = R[:]
f_result = f_function(R, subkeys[i])
R_next = [L[j] ^ f_result[j] for j in range(32)]
L, R = L_next, R_next
# 最后交换(算法中先交换再末置换)
combined = R + L
# 末置换IP^-1
ciphertext = permute(combined, IP_INV)
return ciphertext
# 测试
if __name__ == "__main__":
plaintext_hex = "0123456789ABCDEF"
key_hex = "133457799BBCDFF1"
# 转换为位列表
plaintext_bits = hex_to_bits(plaintext_hex, 64)
key_bits = hex_to_bits(key_hex, 64)
print(f"明文: {plaintext_hex}")
print(f"密钥: {key_hex}")
# 加密
ciphertext_bits = des_encrypt(plaintext_bits, key_bits)
ciphertext_hex = bits_to_hex(ciphertext_bits)
print(f"密文: {ciphertext_hex}")
|